 |  |  |
| Prototype | Botnet threat and BDS operation | PN2Simulator |
 |  |  |
| Prototype | Botnet threat and BDS operation | PN2Simulator |
| Figure 1 presents a PN2 model depicting the example network. This model comprises a central environment net and five surrounding agent nets. The environment net (located in the center) utilizes places (drawn as circles, labeled as P1, P2, and P3) to represent the three nodes (n1, n2, and n3) in the network. Place P1 has two tokens (drawn as ellipses), each of which represents device d1 and a malicious worm infecting it. Place P2 has only one token, which represents device d2 in a normal state. Place P3 has two tokens, each representing device d3 and a white-hat worm infecting it. Each token corresponds to an agent, and its state transitions are detailed by the corresponding agent net. These nets utilize places (drawn as circles) to represent states (e.g., p1 for normal) and transitions (drawn as squares) to depict actions (e.g., t1 for infected). Consider the agent net for device d1. The initial state (p1) signifies a normal device. Transition t1 models the "infected" action, causing the device to transition to the infected state (p2). While rebooting an infected device can return it to normal, there is often a delay between infection and reboot (represented by a path). The path a device takes through the agent net depends on the type of worm infecting it. If infected by a malicious worm, the device progresses through a cycle of states (p1, t1, p2, t2, p3, etc.). However, if infected by a white-hat worm, it follows a different cycle (p1, t1, p2, t2, p3, t6, etc.). White-hat worms possess an additional capability. Triggering secondary infections on devices already compromised by malicious worms (represented by transitions t9, t10, t11, and t12). By adjusting the firing probabilities of these transitions, researchers can control the aggressiveness of the white-hat worm's secondary infection ability. The PN2 model of BDS facilitates the simulation of its behavior through a process called a token game. In this game, red transitions signify that they are currently eligible to fire (executable). Let us focus on transition T113. Firing of this transition indicates that the malicious worm residing on node n1 is attempting to infect device d2 on node n2. T113 represents the interaction between the worm's action "m_infect" and the device's action "infect." Here is why T113 is fireable. A token representing the malicious worm is present at an input place (P1) of T113. The agent net for the malicious worm has a fireable transition (t1) labeled "m_infect." Additionally, a token representing device d2 exists at another input place (P2) of T113. The agent net for device d2 also has a fireable transition (t1) labeled "infect." These conditions collectively enable T113 to fire. | 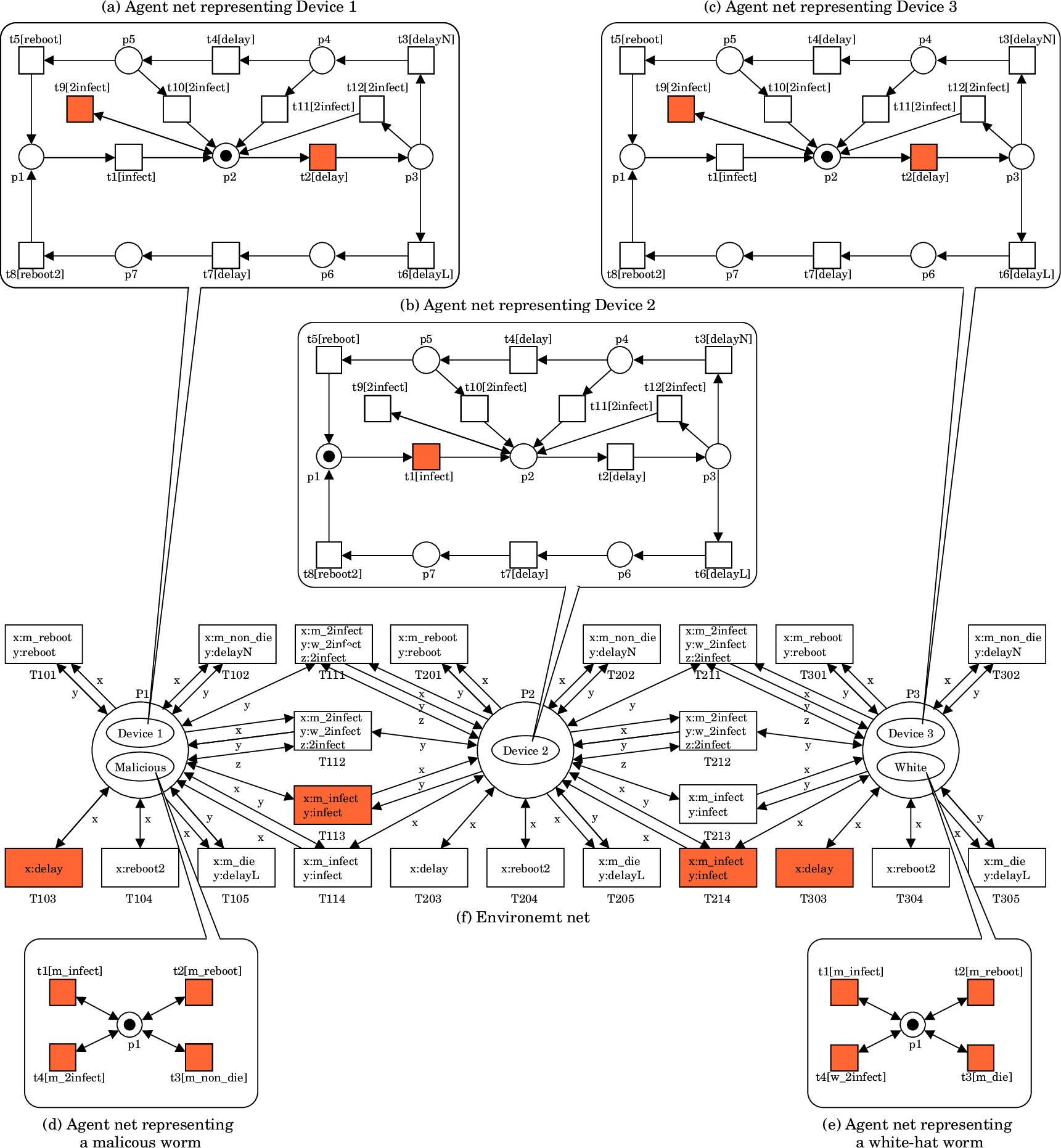 Figure 1: PN2 model representing BDS defending a network composed of three devices. |
PN2Simulator is a software tool that empowers users to edit PN2 models and play interactive token games directly. Figure 2 showcases the PN2Simulator's operation screen.
The screen is divided into two main sections:
|
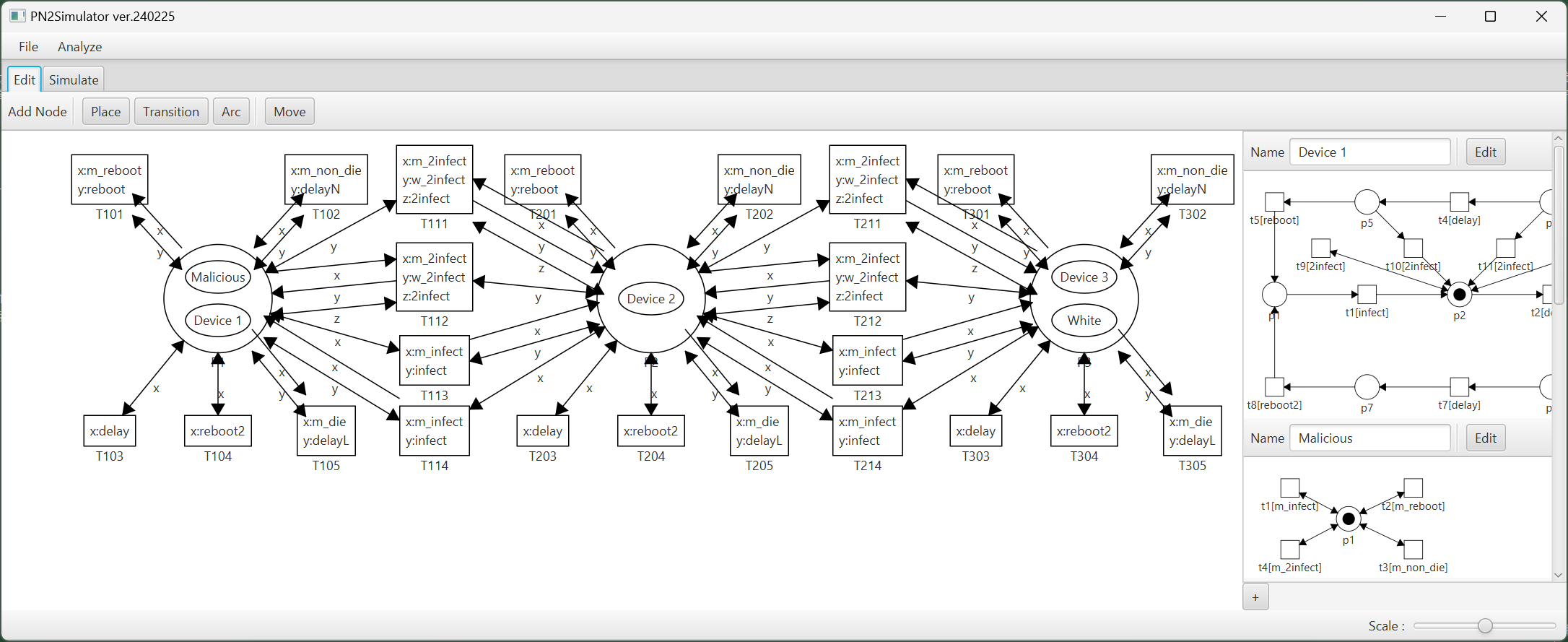 Figure 2: PN2Simulator's operation screen. |
| Figure 3 depicts the PN2Simulator's simulation screen. This screen provides an interactive environment for simulating the behavior of the PN2 model. Transitions highlighted in red signify that they are currently eligible to fire. Clicking on a red transition triggers its execution, simulating the corresponding action within the model. Pressing the "Random" button initiates the random firing of a single transition from the set of currently fireable transitions. Entering a number (n) in the "Count" text field and clicking the "Auto" button simulates n consecutive random firings of transitions. This is equivalent to pressing the "Random" button n times. The simulation screen shows the state after transition T113 fires in the state shown in Figure 1. In this state, the white-hat worm on the central node is attempting to launch a secondary infection on the device located on the left node. Clicking the fireable transition T112 would simulate this attempted secondary infection. This interactive simulation environment empowers researchers to experiment with different scenarios and gain valuable insights into the dynamic behavior of the BDS system. |  Figure 3: PN2Simulator's simulation screen. |
Figure 4 depicts a specific infection scenario involving both a malicious and a white-hat botnet. Here, we assume the following initial state.
|
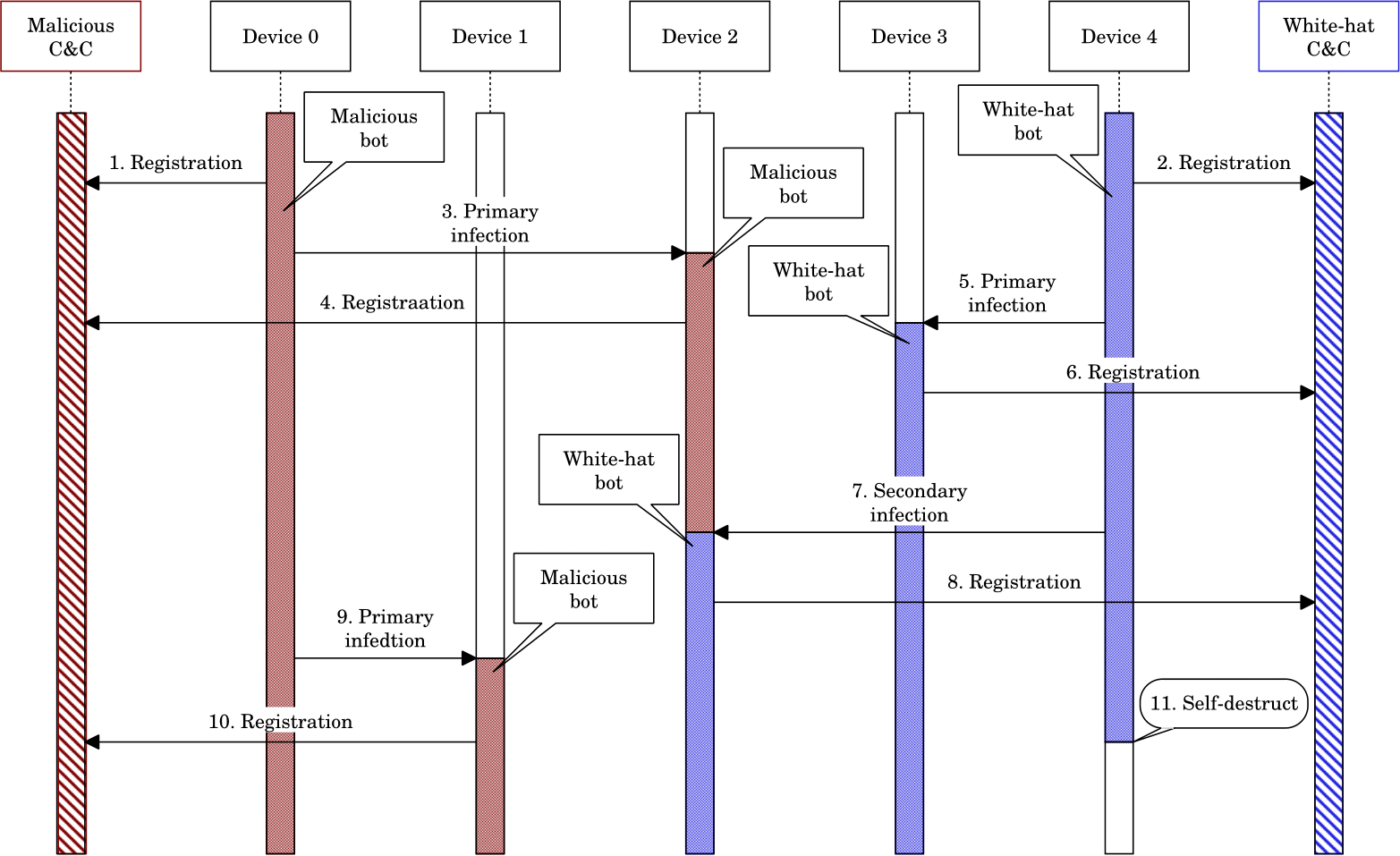 Figure 4: PN2 model representing BDS defending a network composed of three devices. |
|
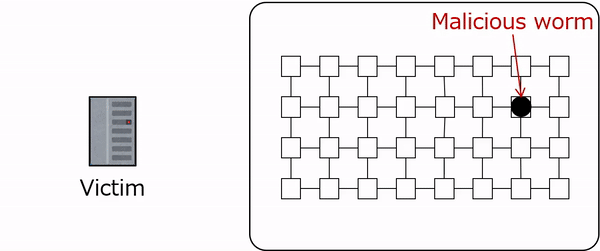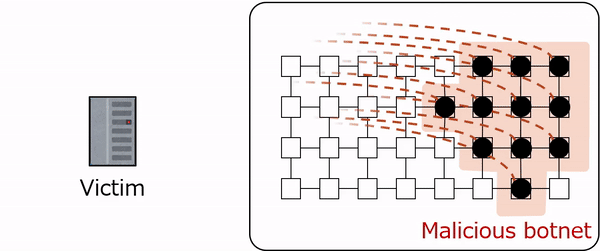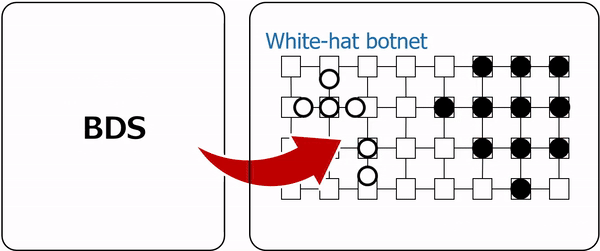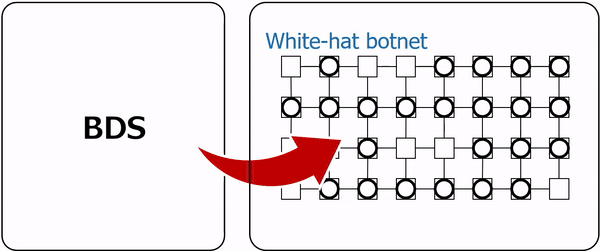
iBDS is an extension of BDS that introduces a new defense mechanism inspired by the bioimmune response, effectively eliminating botnets that repeatedly infect IoT networks. Focusing on the roles of antibodies and phagocytes in the immune response, iBDS implements multi-layered defense using two types of worms: antibody worms and phagocyte worms. When a malicious botnet infects a network, resident phagocyte worms immediately infect and eliminate the bots, preventing the spread of infection in its early stages. This provides an immediate response similar to that of innate immunity. On the other hand, if a malicious botnet infects the network and the phagocyte worms cannot infect the bots, the antibody worms will instead infect the bots and modify their vulnerabilities to enable the phagocyte worms to infect and eliminate them. This provides an adaptive response similar to acquired immunity. Furthermore, if the same botnet repeatedly infects the network, more antibody worms are used to generate a stronger response similar to immune memory. iBDS works according to the following five steps, and Steps 2 through 5 are repeated until the end of the operation.
The network environment was constructed using devices running the OpenWrt operating system, which is widely deployed in commercial routers and IoT devices. A key characteristic of Mirai is that its bots operate as ephemeral processes in volatile memory following device infection, deliberately avoiding storage in non-volatile memory or file systems. Consequently, a Mirai bot can be completely eradicated from an infected device simply by terminating its associated processes. Our proposed phagocyte and antibody worms enact disinfection by identifying the malicious worm's process via the network port it utilizes and subsequently forcing its termination. This design is directly based on the Killer process mechanism present in the original Mirai source code. By automating this process, the proposed worms are capable of efficiently disinfecting devices, significantly reducing the necessity for manual intervention in the event of a large-scale infection. The device vulnerability simulated in this prototype utilized weak login credentials (a common user ID and password combination). Experimental results from simulations and prototype implementations demonstrate that iBDS can effectively eliminate botnets that repeatedly infect IoT networks. |
 Figure 5: Innate immunity of iBDS  Figure 6: Acquired immunity of iBDS |