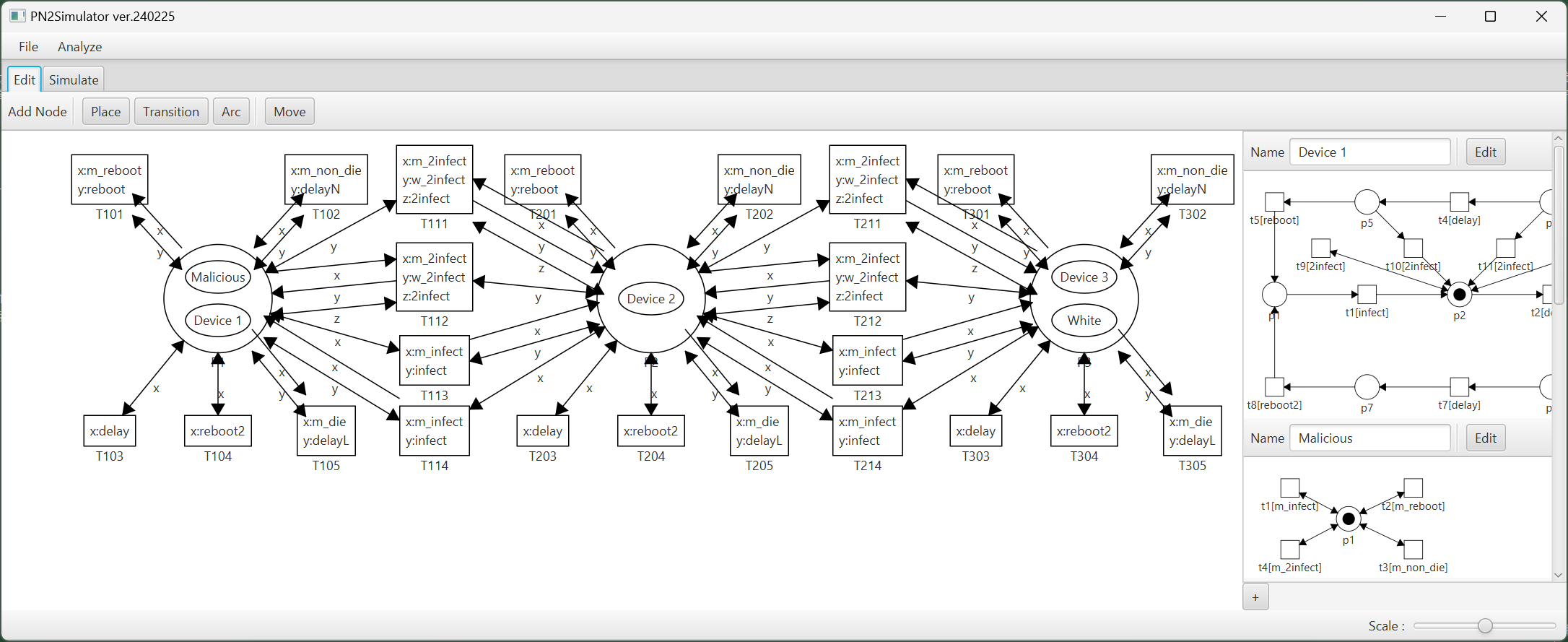
|
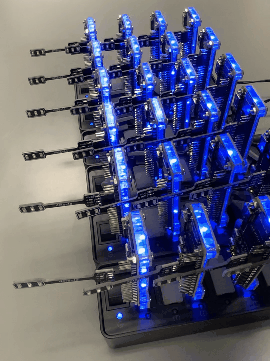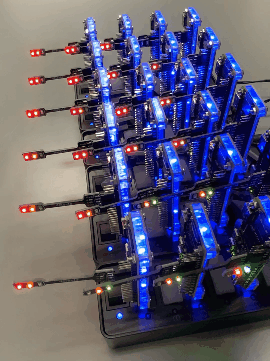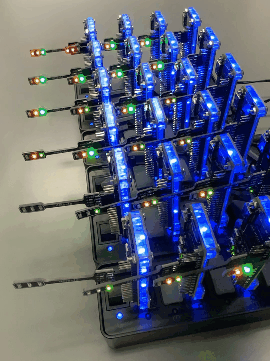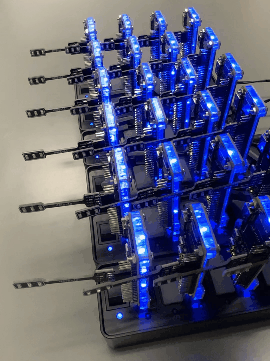
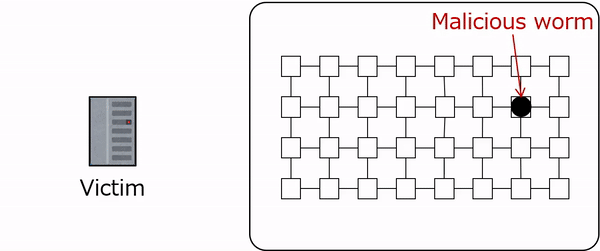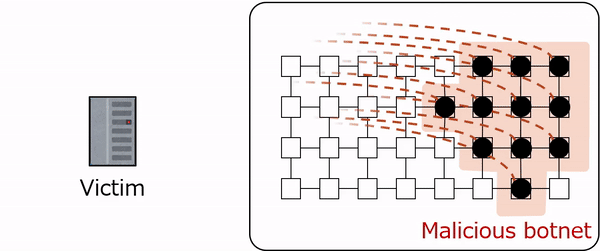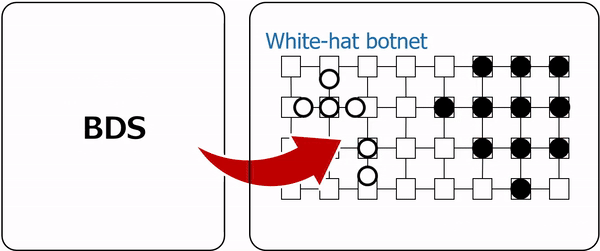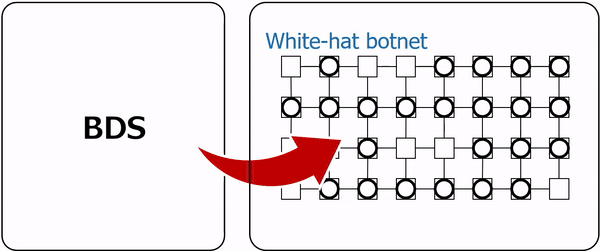
Figure 1 presents a PN2 model depicting the example network. This model comprises a central environment net and five surrounding agent nets.
The environment net (located in the center) utilizes places (drawn as circles, labeled as P1, P2, and P3) to represent the three nodes (n1, n2, and n3) in the network.
Place P1 has two tokens (drawn as ellipses), each of which represents device d1 and a malicious worm infecting it. Place P2 has only one token, which represents device d2 in a normal state. Place P3 has two tokens, each representing device d3 and a white-hat worm infecting it. Each token corresponds to an agent, and its state transitions are detailed by the corresponding agent net.
These nets utilize places (drawn as circles) to represent states (e.g., p1 for normal) and transitions (drawn as squares) to depict actions (e.g., t1 for infected).
Consider the agent net for device d1. The initial state (p1) signifies a normal device. Transition t1 models the "infected" action, causing the device to transition to the infected state (p2). While rebooting an infected device can return it to normal, there is often a delay between infection and reboot (represented by a path).
The path a device takes through the agent net depends on the type of worm infecting it. If infected by a malicious worm, the device progresses through a cycle of states (p1, t1, p2, t2, p3, etc.). However, if infected by a white-hat worm, it follows a different cycle (p1, t1, p2, t2, p3, t6, etc.).
White-hat worms possess an additional capability. Triggering secondary infections on devices already compromised by malicious worms (represented by transitions t9, t10, t11, and t12). By adjusting the firing probabilities of these transitions, researchers can control the aggressiveness of the white-hat worm's secondary infection ability.
The PN2 model of BDS facilitates the simulation of its behavior through a process called a token game. In this game, red transitions signify that they are currently eligible to fire (executable).
Let us focus on transition T113. Firing of this transition indicates that the malicious worm residing on node n1 is attempting to infect device d2 on node n2. T113 represents the interaction between the worm's action "m_infect" and the device's action "infect."
Here is why T113 is fireable. A token representing the malicious worm is present at an input place (P1) of T113.
The agent net for the malicious worm has a fireable transition (t1) labeled "m_infect."
Additionally, a token representing device d2 exists at another input place (P2) of T113.
The agent net for device d2 also has a fireable transition (t1) labeled "infect."
These conditions collectively enable T113 to fire.
|
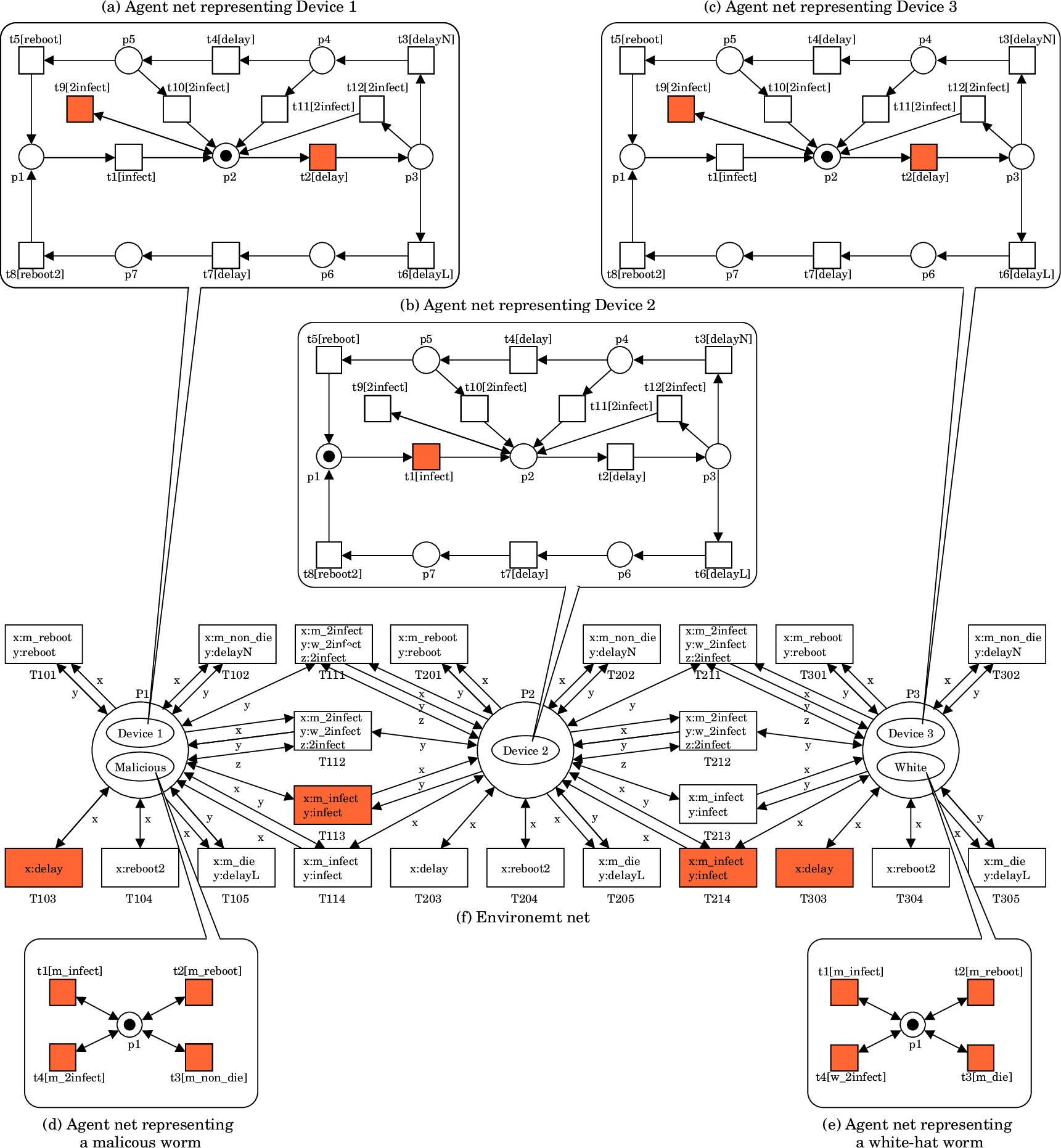
Figure 1: PN2 model representing BDS defending a network composed of three devices. |